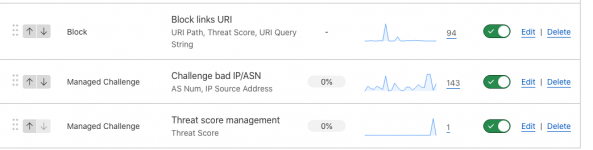
One feature I love about CF is the ability to block entire ASN's as well as specific IPs.
A few of the more recent that I have added as I get a LOT o "crap" from servers in their data centers (and since those aren't users, I don't have issues with blocking the entire ASN) are:
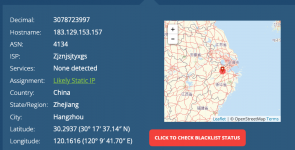
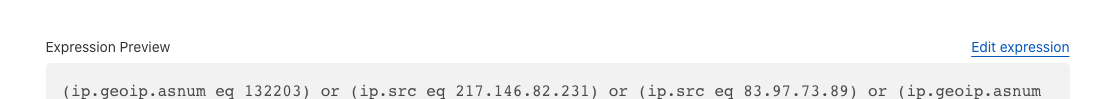
132203 (TENCENT-NET-AP-CN - China)
45899 (VNNIC-ASBLOCK-VN - Vietnam)
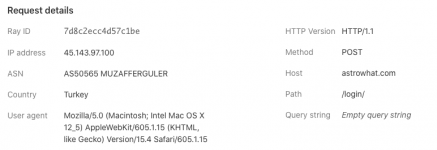
50565 (MuzafferGuler - Turkey)
135407 (TES-PL-AS-AP - Pakistan)
208312 (Red Byte LLC - Russia)
35913 (DEDIPATH-LLC - United States)
149428 (CODE200-AS-AP - Lithuania)
21859 (ZEN-ECN - United States)
22363 (POWER157 - United States)
136557 (HOST-AS-AP - Australia)
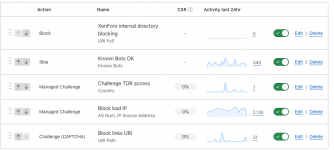
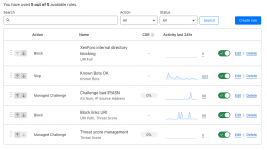
I don't do a full block... but they do have to go through a interactive challenge to get to the site. Since I've done this, a lot of my 404 errors (tracked by an add-on) to the site have bit the big one.
These are some of the attempts that have been presented:
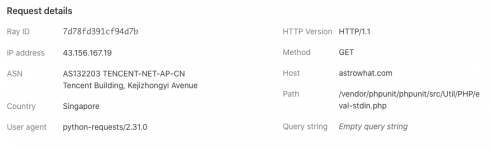

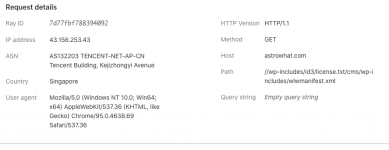
Many of these are simply bots running out of data centers looking for an ingress point. With CF, you can block them totally or allow access based upon certain criteria.
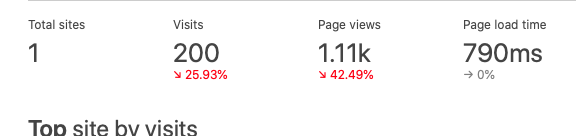
Just to give an idea... I implemented these about 2 days ago.
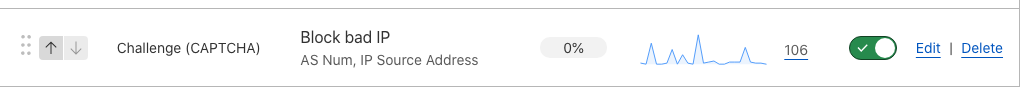
I run the "good bots" on CF, but anything else that is being used, I really don't want wasting the time of my site.
The main portion of these are data centers... which honestly have NO reason to be accessing your site as a "user"... if you see them, then they are typically a bot working to spam your site.
So, what ASN's have you blocked?
A few of the more recent that I have added as I get a LOT o "crap" from servers in their data centers (and since those aren't users, I don't have issues with blocking the entire ASN) are:
132203 (TENCENT-NET-AP-CN - China)
45899 (VNNIC-ASBLOCK-VN - Vietnam)
50565 (MuzafferGuler - Turkey)
135407 (TES-PL-AS-AP - Pakistan)
208312 (Red Byte LLC - Russia)
35913 (DEDIPATH-LLC - United States)
149428 (CODE200-AS-AP - Lithuania)
21859 (ZEN-ECN - United States)
22363 (POWER157 - United States)
136557 (HOST-AS-AP - Australia)
I don't do a full block... but they do have to go through a interactive challenge to get to the site. Since I've done this, a lot of my 404 errors (tracked by an add-on) to the site have bit the big one.
These are some of the attempts that have been presented:



Many of these are simply bots running out of data centers looking for an ingress point. With CF, you can block them totally or allow access based upon certain criteria.
Just to give an idea... I implemented these about 2 days ago.

I run the "good bots" on CF, but anything else that is being used, I really don't want wasting the time of my site.
The main portion of these are data centers... which honestly have NO reason to be accessing your site as a "user"... if you see them, then they are typically a bot working to spam your site.
So, what ASN's have you blocked?
Last edited: